The digital world promised connection and convenience, and it largely delivers. However, this interconnectivity has also created fertile ground for scams and online fraud to, well, thrive. The numbers are frankly alarming. The reported fraud losses surpass billions of dollars yearly and paint a troubling picture. However, what if I told you that victimization does not have to mean that you are stuck?
During my work as a digital investigator, I’ve often seen that people are able to reclaim agency. Often, victims of cybercrime can proactively search for who scammed them and possibly recoup lost funds.
Think back to the beginning of your search for money or love… or perhaps your search for help. It is important to know that you are not alone. It is a difficult climb out of financial ruin, especially if it was built on fraud. Scammers can make it seem like there is no option other than to succumb to their demands. They make it seem like no one but them can help you. However, knowledge and resilience can provide the strength to resist them.
There’s hope, and there’s significant action you can take. Start by learning the strategies scammers use, so you are the one armed with knowledge. It is possible to minimize losses and gain the resources for victim empowerment and minimization of fraud!
Understanding How Scams Work: Common Scam Tactics and Techniques
Scams are masters of disguise, constantly evolving their methods, but at their core, they share the same dark objective. They deceive you to steal your money or personal information. It might be worthwhile to delve into the anatomy of a few popular scams so you can protect yourself.
Phishing scams are a really common example; these are those deceptive impersonations of legitimate organizations via email, text, or even phone calls. Their goal? To trick you into willingly handing over sensitive stuff like passwords, credit card deets, or your Social Security number. Imagine this: you get an email that looks incredibly official, purporting to be from your bank. It frantically warns you of “suspicious activity” and urges you to click a link, pronto, to “verify” your account. Sounds routine, right? Except… that link leads to a cleverly crafted fake website. One that is specifically designed to steal your stuff.
Then there are romance scams. These prey on something that is very deeply human: our need to connect with others. With romance scams, criminals put on a mask. Scammers create fake online profiles, building emotional connections with their targets. Once they’ve cultivated trust-oh so carefully-the requests for money start. Elaborate stories of fabricated emergencies, urgent travel needs, or family crises follow. It’s chilling how they exploit vulnerability.
And let’s not forget about the allure of quick wealth: investment scams. These lure people in with false assurances of really high returns and profits that seem too good to be true (because they are!). Quite often they try to push you to invest quickly before conducting your research.
Recognizing Red Flags: Spotting a Scam Before It’s Too Late
Prevention is undoubtedly the best and easiest medicine when it comes to scams. However, how can you tell what a scam looks like so you can prevent it?
Here is what you should look out for:
- Typos and grammatical errors: Okay, so this one might seem like a minor detail, but it’s often a telltale sign. Legitimate organizations invest in professional communication. Sloppy writing often = scam.
- Requests for personal information: This is a HUGE one. Be extremely cautious of any unsolicited requests for sensitive data like your Social Security number, bank details, or passwords. Legitimate businesses rarely ask for this stuff out of the blue. And Experian says the same thing!
- Pressure to act quickly: Creating a sense of urgency is a classic manipulation tactic, as noted by dev.to. Scammers don’t want you to have time to think, research, or consult with someone you trust.
- Unsolicited offers or prizes: If it sounds too good to be true, it almost always is. Be skeptical of unexpected offers, especially if you need to pay a fee to “claim” them.”
Immediate Steps to Take After Being Scammed: Preserving Evidence and Documenting Everything
Time is of the essence if you think you have been scammed. One of the key aspects to remember is documenting everything. Every. Single. Detail. This isn’t just about remembering what happened; it’s about creating a strong record that can be used to track down the scammers.
Preserve communications to the best of your abilities so that the fraudster does not remove or redact them. Emails, texts, social media conversations – all these serve as valuable pieces of evidence. Take full-screen captures of your computer screens. Save your emails as files. Keep details from the interactions you had with the criminal. Every “promise”, every “request,” every “detail”. Keep track of the interactions you have had. This helps to create a timeline.
Oh, and here’s a slightly geeky tip: Metadata can be your friend. Metadata is the embedded data that is stored within digital files. This can contain information such as authorship, timestamps, and locations. If you have the resources, it can be used to verify the authenticity of the documents you collect.
Freezing Accounts and Changing Passwords
Once you have gotten the receipts, it is important to act quickly!
Did you know that financial institutions have fraud departments to help you cancel credit and debit cards? Banks and credit companies are your advocates in these situations! It’s time to give them a call as Experian has noted in their articles.
Next, you need to make sure those criminals stay away from your accounts! What did you use for a password? Make sure it isn’t easily guessed! Identity Guard has more information on how to determine what to do to change bad passwords. Create new ones that you do not use for anything else.
Taking these protectionary measures will minimize damage and help protect you from identify theft.
Gathering Information: Tracing the Scammer’s Digital Footprints – Open Source Intelligence (OSINT): Leveraging Publicly Available Information
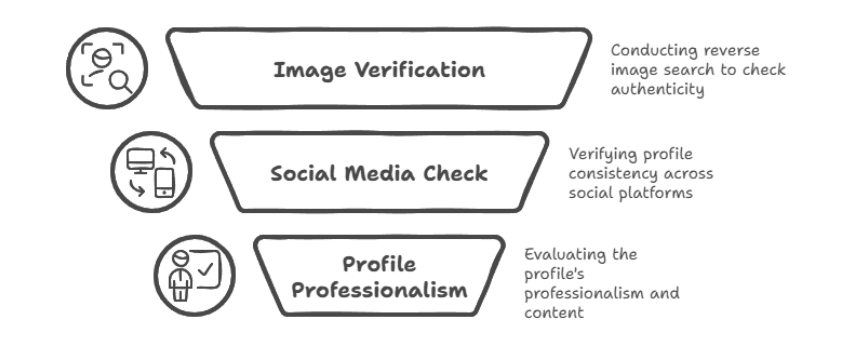
Now comes the part where you put on your detective hat. It involves piecing together the scammer’s digital footprint by using open-source intelligence (OSINT) techniques. What does this mean? It means collecting information from public sources such as social media platforms and public records databases.
One really helpful technique is reverse searching to find their images. All you have to do is upload photos to search engines to determine if more information can be found online. Social Media investigations are also helpful. Even if the person is using a fake name, social media connections or patterns might lead you to who they truly are.
An account of when someone used open-source intelligence to recover their stolen image is cited within the osintteam blog.
Following the Money: Tracing Financial Transactions
Oh, the sweet, sweet money… Or the absence thereof… I’m going to be honest, tracing money is like trying to follow a drop of water in a hurricane, especially when cryptocurrency is involved. However, don’t let that deter you. Let’s break this down, because whether it’s a standard bank transfer, a crypto transaction, or even the purchase of gift cards, there might be a breadcrumb trail.
With traditional bank transfers, contact the bank and request a trace on the transaction. However, the bank might not be able to provide much due to privacy protocols.
Tracing the funds when it comes to cryptocurrency is also possible through the use of blockchain analysis tools. When you find something you might deem, “sketchy”, look for red flags such as transactions to unregulated exchanges or mixing services,
Reporting the Scam to Authorities and Institutions
Even though it is a hard hit to the stomach, reaching out to law enforcement helps not only your case but the cases of others.
Reporting to Law Enforcement: Filing a Police Report
When reporting to law enforcement, filing a case is important, even if it might not yield immediate results. It documents that you were scammed and contributes to the overall fight against fraud. You want to first contact your local police department or give a ring to the police department in the scammer’s location (if known). They can help build a thorough record for if the scammer is apprehended in the future.
It should be noted that you can include a police report on your linkedIn profile.
Reporting to Federal Agencies
In addition to the authorities in your city, there are state authorities to consider also. The Federal Trade Commission (FTC) is a primary resource for reporting fraud and scams in the United States. The FBI’s Internet Crime Complaint Center (IC3) is also good to report significant losses to.
Contact your bank’s fraud department to report any scams and reviews of recent transactions right away as cited in Consumer Finance gov. You can also include fraud alerts to prevent the scammer from pursuing cases in your name.
Advanced Techniques: Digital Forensics and Expert Help – Understanding Digital Forensics
Have you ever heard of digital forensics? You might have seen it on TV. Digital forensics is the science of looking for evidence on computers and digital devices.
For example… What could happen if digital forensics was used to protect you? What if a scammer asked you to download remote access software on your computer? Digital forensics could be used to protect you! A digital forensics expert can help determine what data was used when they had access. This information could then be used to prosecute the scammer. The hackers pro also cited that digital forensics can assist businesses and the like if individuals happen to be hacked.
Sometimes, you don’t even know you need an expert… A victim of a phishing scam removed the criminal’s emails, believing they were doing the right thing to protect themselves. After a digital forensics examination was done, it was determined that an IP address and location was determined.
When to Seek Expert Assistance
There are some things you can do on your own, but you definitely have to bring in the big guns at some point. As the experts at digitalinvestigation dot com say, “a professional investigator can conduct in-depth research and surveillance to uncover the scammer’s identity and location digitalinvestigation.com”. Consult with those who bring some experience to the table.
Legal Options: Exploring Options for Recourse
You’ve been wronged, you’ve reported it, what else can you do?
Civil Lawsuits: Suing the Scammer for Damages
One potential way to recover funds is a civil lawsuit. However, scammers often operate under fake names. This is a major challenge. Also, even if you are able to identify the scammer, they might have gotten away with the money already if they moved it offshore. Before pursuing a case, weigh the pros and cons of legal fees.
You can also work with law enforcement to bring criminal charges against the scammers based on material that might be cited within Vocal Media. This might entail imprisonment.
Protecting Yourself from Future Scams Recognizing Red Flags and Avoiding Suspicious Offers
The best way to protect yourself is to remember scams in the first place! If a deal is “too good to be true”, it probably isn’t good. And NPR stated how important that concept is.
Here’s what to remember in case you thought I wasn’t clear the first time:
- Mistake: Clicking links from unsolicited emails / texts.
- Avoidance: Instead, go directly to the website of whom you are looking for.
- Mistake: Giving away sensitive personal information such as passwords and bank information.
*Avoid giving out personal information to someone that called you.
- Mistake: Investing in opportunities without researching it.
- Avoidance: Do your research before investing.
- Mistake: Getting peer pressured into a sale you aren’t sure of.
- Avoidance: Take your time to evaluate.
- Mistake: Ignoring the bad grammar in written communications.
- Avoidance: Legitimate companies and organizations have good grammar and proofread their work.
Implementing Security Measures: Protecting Your Data and Devices
It’s not just about knowing the tricks, but also about setting up a good defense. Put up walls!
Installing a good antivirus software system is crucial. Make sure you give your online accounts unique and easy-to-guess passwords. Set up multi-factor authentication to protect all that you have. ASsets DOT mydataremoval DOT COM does a good job of explaining MFA as well.
Look, getting scammed is awful. It’s disorienting, and it can leave you feeling violated. But remember, scams happen to many people – even those with some life experience. They happen because scammers are masters of manipulation.
Protecting your information, seeking help with agencies and cyber experts, and consulting with individuals are just some of the methods to help combat fraud in the digital age. And remember by knowing your rights and being vigilant, you CAN reclaim the story.